Rocket® z/Assure® Vulnerability Analysis Program (VAP)
VAP helps businesses identify, assess, and mitigate security vulnerabilities within their systems, ensuring a robust and secure IT environment with mainframe vulnerability scanning.
Why mainframe security matters
Did you know that up to 71% of a corporation's financial data can be stored on the mainframe? Contrary to popular belief, mainframes can be breached. Many organizations, misled by myths, neglect mainframe security, leading to potential breaches. Every z/OS environment has vulnerabilities - once exploited, hackers can access any data within.
Fortify defenses. Without the oversights
Elevate your mainframe’s security posture with Rocket z/Assure VAP, ensuring your system remains resilient against modern threats while optimizing its performance with mainframe vulnerability scanning.
- Automated, real-time, binary code scanning: We make it possible for enterprises to scan the operating system layer of the mainframe to identify zero-day vulnerabilities without the use of signature files.
- Precise vulnerability detection: Utilize the power of the Interactive Application Security Testing (IAST) model, pinpointing real vulnerabilities and guiding developers directly to the issues.
- Detailed vulnerability reports: Empower your teams with comprehensive insights, streamlining the path to immediate remediation.
- Proactive defense strategy: By understanding and debunking the myths around mainframe security, z/Assure VAP ensures a proactive approach to strengthening defenses with mainframe vulnerability scanning.
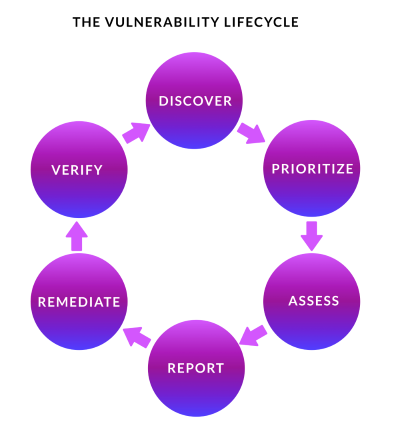
How z/Assure VAP works
Manually scanning systems isn't just time-consuming—it's impractical. Rocket Software advocates for a systematic, automated approach:
- Initiate a baseline scan of your enterprise.
- Review the Vulnerability Detail Reports (VDRs).
- Engage with vendors using VDRs.
- Implement patches from vendors.
- Rescan to confirm vulnerability resolution.
- Regularly scan before maintenance is applied into your production environment.
Questions IT Risk Officers can ask
to determine gaps
Q1: Is the mainframe environment a part of your IT Risk Assessment methodology?
Q2: Does your compliance and risk team provide you with ongoing mitigation reports associated with operating system risks?
Q3: Do you have the proper controls, governance, and communication to leadership on all aspects of securing your mainframe environment?
Q4: Do you have a Mainframe Vulnerability Management Program? If not, what aspects of the mainframe are included in compliance audits?
Q5: Do you have compliance solutions that utilize the commonalities in all the compliance regulations?