Unveiling Database Corruption: Understanding the Process and Solutions
This is a multi-part series by Bruce Decker on Protecting Your Business, A Practical Guide to System Recovery.
Read the entire series in the on the Rocket Software website.
In the world of databases, corruption can wreak havoc on critical business operations. While backups and replication strategies are essential, understanding how databases become corrupt sheds light on effective solutions like Database Journaling and Replication.
Many data storage engines use operating system files as a storage object. Internally, a UNIX file looks like this:
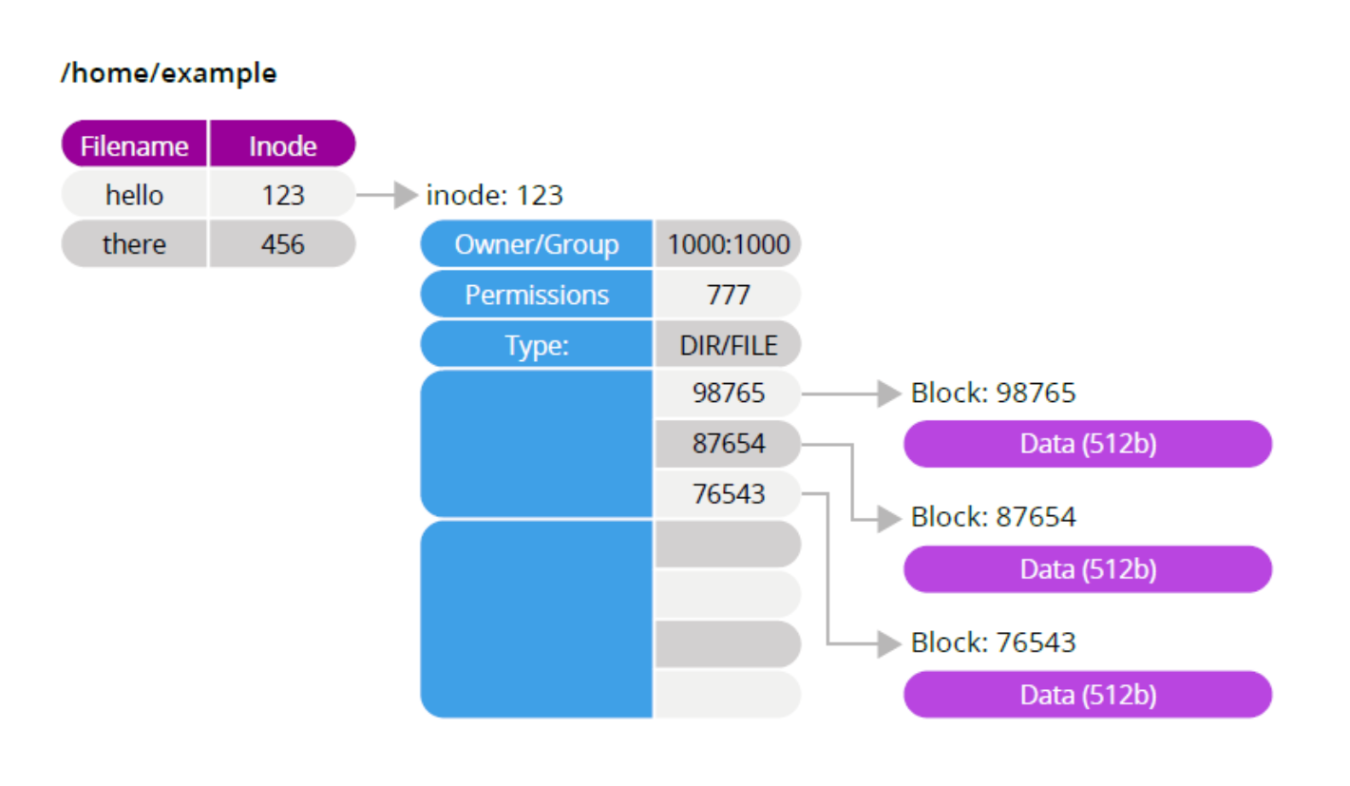
1. Database vs. Operating System Files:
A database, designed for rapid data state changes, stores records securely on disk, outperforming regular operating system files.
Operating system files, like UNIX files, manage data using blocks, each containing information about the file's ownership, permissions, and data location.
2. Database Management Process:
Databases organize data across blocks within UNIX files, managing the storage and retrieval process efficiently.
When applications interact with the database, they handle records, leaving the database manager to manage block-level operations seamlessly.
3. Corruption Risks:
Large records or rapid data updates can lead to partial block updates within the database file.
Hardware-level replication, unaware of block linkages, can trigger replication events before all blocks are updated, resulting in database corruption.
4. Preventive Measures:
Suspending updates and flushing blocks to disk ensures all changes are committed, maintaining database integrity.
However, frequent database pauses for snapshot events may not be practical for most businesses during regular operations.
Understanding the intricacies of database management and corruption risks equips businesses with the knowledge to implement effective preventive measures, safeguarding critical data integrity.
Related posts
ERP in the Cloud Era
Why Turn to AI in Workload Automation
Rocket® AI Predictive Pulse is an add-on for Zeke, Enterprise Orchestrator, and Zena.
Enhancing Zeke with AI Predictive Pulse
AI Predictive Pulse helps users proactively address issues, optimize workflows, and improve system reliability.