The New NIST Password Guidelines, Automatic Data Encryption and You
NIST
The National Institute of Standards and Technology (NIST) is a United States Government organization, part of the U.S. Department of Commerce. One of the many functions of NIST is cybersecurity. They publish standards and sets of guidelines to aid companies in their cybersecurity endeavors. They also publish recommendations for passwords. While NIST is a U.S. based organization, their recommendations, standards, and guidelines are used by cybersecurity professionals the world over.
Recently, NIST has redefined their password recommendations. In August this year (2024), NIST published Special Publication 800-63B (SP800-63B) which includes some interesting changes to password creation and management. Some might say a ‘relaxing’ of certain guidelines we’ve all come to take as law for years now.
NIST Special Publication 800-63B
Encryption in U2 databases
Rocket U2 Automatic Data Encryption comes with a password policy feature that allows you to enforce certain rules on passwords for encryption keys, encryption wallets and the master key. These items can be defined separately with their own set of rules. Users of Rocket UniData and Rocket UniVerse can set these policy rules using the Rocket U2 Extensible Administration Tool, or the command line ‘encman’ utility. They come with default parameters that were inline with previous NIST recommendations.
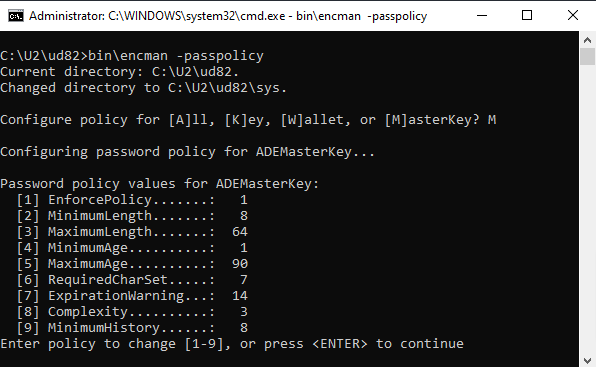
Figure 1: Default password policy rules - 'encman -passpolicy'
New recommendations
According to NIST’s new guidelines, several of the more tedious rules are no longer a requirement.
Complexity: Previously, it was recommended that a mix of uppercase and lowercase letters, numbers and special characters were mandatory in all passwords. The focus is now on password length rather than complexity. It was found that users were unable to remember complex passwords and so tended towards shorter, predictable patterns. The hope now is that users will choose a longer passphrase that is easier for them to remember but more difficult to break using brute force or to guess: “P4ssw0rd!” vs. “my first dog was called fido”.
Length: Related to the complexity recommendation is the length of a password. Eight has been the magic number for a long time and it is still recommended as the absolute minimum. However, with a move towards passphrases, developers are now suggested to allow up to sixty-four characters, enforce an eight-character minimum and are recommended to enforce a minimum of fifteen.
Age: This is potentially an end to the regular “You have x days to change your password” message that some users dread. The feeling from NIST is that users tend to make only minor changes to their password and choose weaker passwords overall when forced to change them. The recommendation now is to choose a long, strong password and leave it alone unless it is compromised. There are regularly updated ‘blocklists’ of weak or compromised passwords that developers can integrate into their application.
There are other recommendations that don’t come under the Rocket U2 Automatic Data Encryption Password Policy scope:
Suggestion to not use password hints or knowledge-based password recovery questions; this type of back door allows an attacker to get a user’s password by having some other information about them (their mother’s maiden name, where they went to school, a pet’s name, etc.).
Storing passwords should use salted hashing; this makes it harder to crack a password using brute force as the calculations are so resource intensive, they make the operation too costly.
All ASCII and Unicode characters, including space, should be accepted in passwords; this allows for lengthy pass phrases that are easy to remember but difficult to guess.
By default, the Rocket U2 Automatic Data Encryption Password Policy settings will enforce:
- A minimum length of 8
- A maximum length of 64
- A minimum age of 1
- A maximum age of 90
- A required character set of uppercase, lowercase, and number (value 7)
- A complexity blocking the account or key name be present in the password (value 1)
- A complexity blocking the use of character succession (value 2)
- A minimum re-use restriction on the last eight passwords
Only a few changes are necessary to bring the policy inline with NIST’s new recommendations.
Length:
While already at the minimum of eight, fifteen is the recommendation for minimum. The maximum is already at the recommended sixty-four.
encman -passpolicy ALL MinimumLength 15
Age:
The MinimumAge setting defines the number of days that must pass after a password is changed before it can be changed again. The new recommendations do not specify anything in this regard however having this at a positive number will stop the password being changed in quick succession. A zero will allow changes immediately after a change.
encman -passpolicy ALL MinimumAge 0
The MaximumAge setting defaults to ninety days, with the new recommendations this can be set to zero (unlimited/no expiry).
encman -passpolicy ALL MaximumAge 0
Complexity:
This is covered by two parameters: RequiredCharSet and Complexity. Complexity refers to the use of the key or account name in the password and using successive characters. The latter has been relaxed. It is still not recommended to use text that includes the key’s name, the account name or the user’s name. The successive character restriction can be removed, while leaving the account/user/key name setting in place, by setting Complexity to 1.
encman -passpolicy ALL Complexity 1
The RequiredCharSet setting dictates the characters required. This is not required in the new recommendations. At the time of writing, a setting of zero is not possible, making it impossible to set a truly unrestricted policy. A setting of two enforces only lower case so is recommended if wishing to make this change. The only passwords that will be blocked for character set reasons will be those containing no lowercase characters at all.
encman -passpolicy ALL RequiredCharSet 2
Note that all the above commands will apply the policy to ALL the password types. To set each one individually (allowing you to set different rules for each) substitute ‘ALL’ with your desired password type:
ADEKey – Encryption Key Passwords
ADEWallet – Encryption Wallet Passwords
ADEMasterKey – Master Key Passwords
The encman utility also has an interactive mode; simply run ‘encman -passpolicy’ to enter this mode. The Rocket U2 Extensible Administration Tool can also be used.
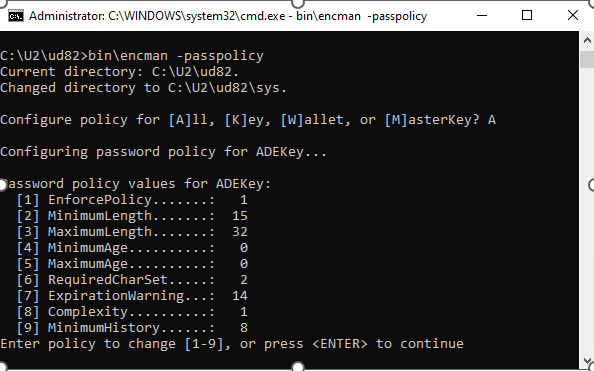
Figure 2: The new recommendations displayed in 'encman -passpolicy'
The approach of NIST when making these changes seems to lean more toward making it easier for users so they don’t break the previous rules. Some feel that relaxing password requirements for these reasons is equivalent to not wearing a seatbelt because you might wrinkle your clothes. But for the most part, these new recommendations have been met with positive feedback by the cybersecurity community.
Rocket Software provides the above purely as informational and not as a recommendation. Set your password policies with caution!
Related posts
AI Innovations
At Rocket Software, we deliver uniquely human and trusted AI solutions to modernize infrastructure, applications, and data with confidence.
Solutions Designed to Empower Developers and Scale IT Impact
Highlighting recent updates and enhancements to Rocket Software’s Skills & Efficiency solutions designed to help fuel even greater innovation.
Understanding the AI-driven Prompt Engineering competency framework
In the field of Generative AI, the industry is working on materials to support Process Engineering as a required hard skill.